Terraform is a terrific configuration management tool. This is probably the best choice if you know your infrastructure and are ready to manage it as a code. And if we are talking code, let's see how you can keep sensitive information away from your code repository.
Terraform allows you to decalre variables and use them to configure your target environment. Variable could have a default value, value declared in one of .tfvars file, or Terraform will ask you to enter missing value during the plan phase. This approach allows you to keep your sensitive input details separate from the source code in the repository.
With all this in mind, my Oracle OCI Terraform variable declarations looks similar to the diagram below.
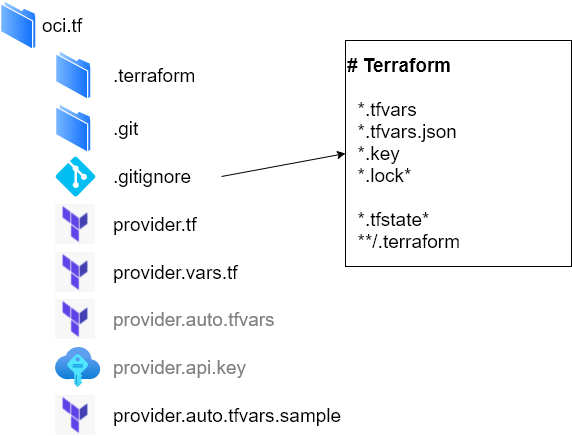
The provider declaration contains two files - module definition and variables declaration (provider.tf and provider.vars.tf). The specific variable values are in the separate file - provider.auto.tfvars. To exclude sensitive content from the source code, .gitignore has exclude rules for all *.tfvars definitions.
Hoverer, I still want to maintain the list of variables required by the configuration, so there is a sample definition - provider.auto.tfvars.sample. It is a template with all the necessary inputs. So for the new project I clone repository, rename the sample file and populate it with the project specific details, plus other sensitive files as private keys.
Of course, for a full scale projects and complex implementation scenarios you should look to specialized solutions such as Hashicorp Vault or AWS Secrets Manager. Even then it is a good practice to keep separate definition of configuration, variables, and input values.
