Enforce HTTPS With OCI Load Balancer
To enforce secure connection you should enforce rewrite rules to rout your clients toward secure listener. The same could be done with load balancer in Oracle Cloud.

Could you remember the last time you typed the URL with the protocol prefix? The modern browsers can test both HTTP and HTTPS and choose one for you. Yet it's the application responsibility to enforce secure connection. So, you should apply rewrite rules to make sure that all your clients use only encrypted connections. Let's see how you can achieve the same with the Oracle Cloud's load balancer.
I presume that you already have a back-end server and an HTTPS listener with all certificates and mappings. So we start with the new ruleset for your load balancer and we start with a new redirect rule:
- Open Networking -> Load Balancers and click on your load balancer to open the details page.
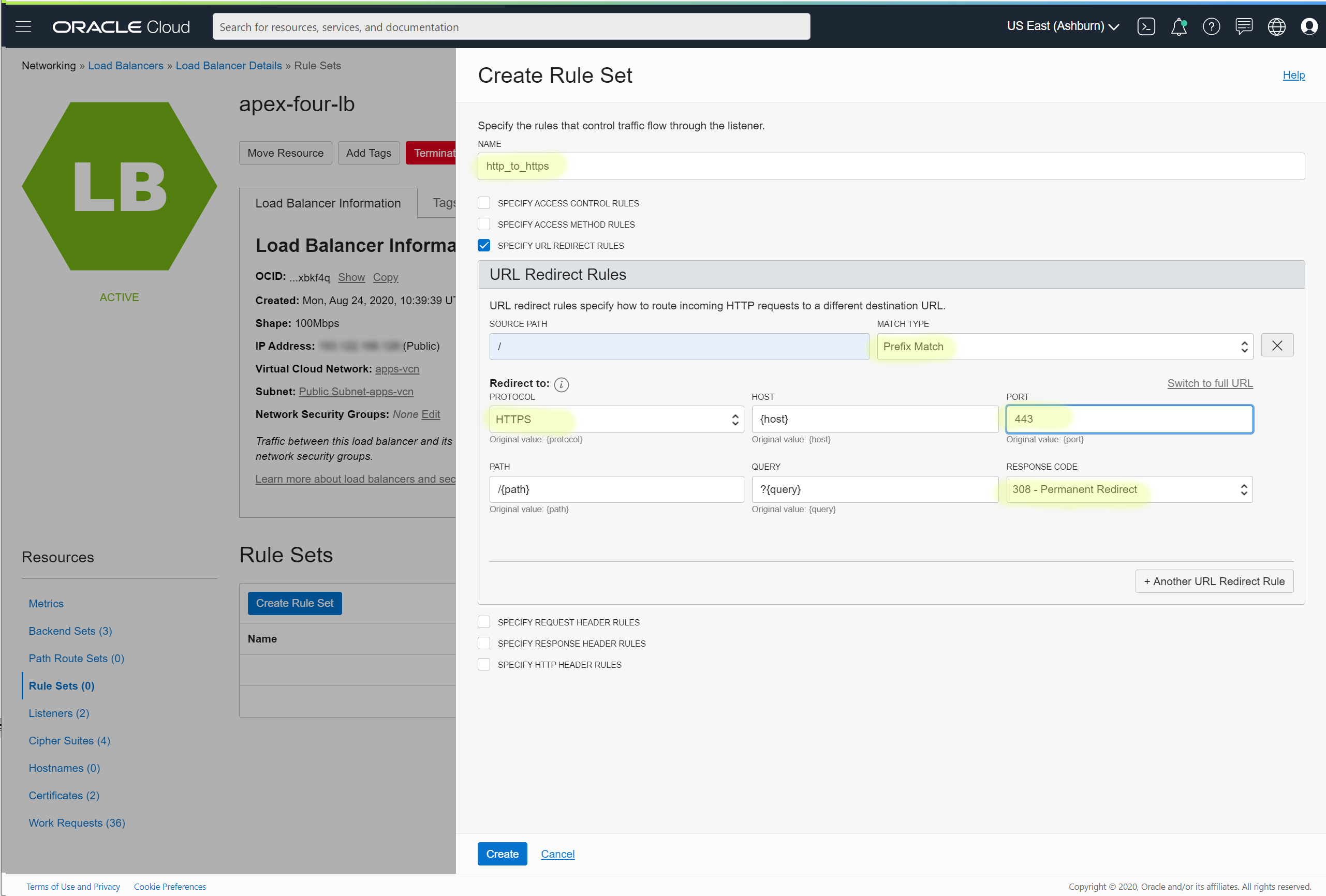
- From the Resources pane, select Rule Sets and then click the Create Rule Set button.
- Choose some name and select SPECIFY URL REDIRECT RULES checkbox.
- You cannot leave SOURCE PATH filed blank, so put / character and change MATCH TYPE to the Prefix Match
- For the redirect: PROTOCOL to HTTPS, PORT to 443, and RESPONSE CODE to 301.
- Click Create when you are ready
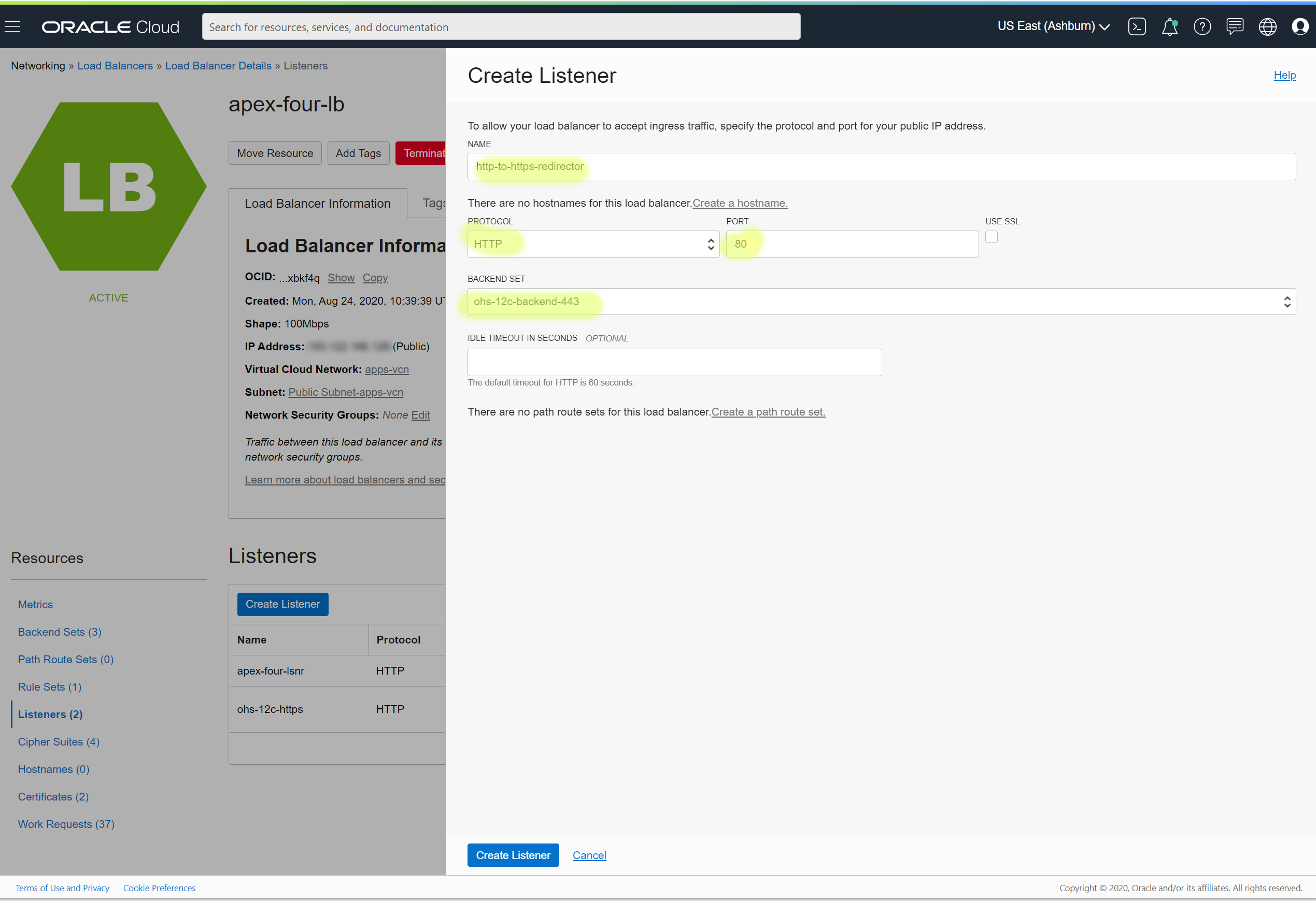
Click on Create Listener button. Give it some name and define the new HTTP protocol and port; select an existing back-end definition; it wouldn't serve any requests anyway.
When a new listener appears in the list, select Edit from the context menu on the right.
Click the button + Additional Rule Set and select the rule you've just defined. Update listener configuration and give a few seconds to complete work requests.
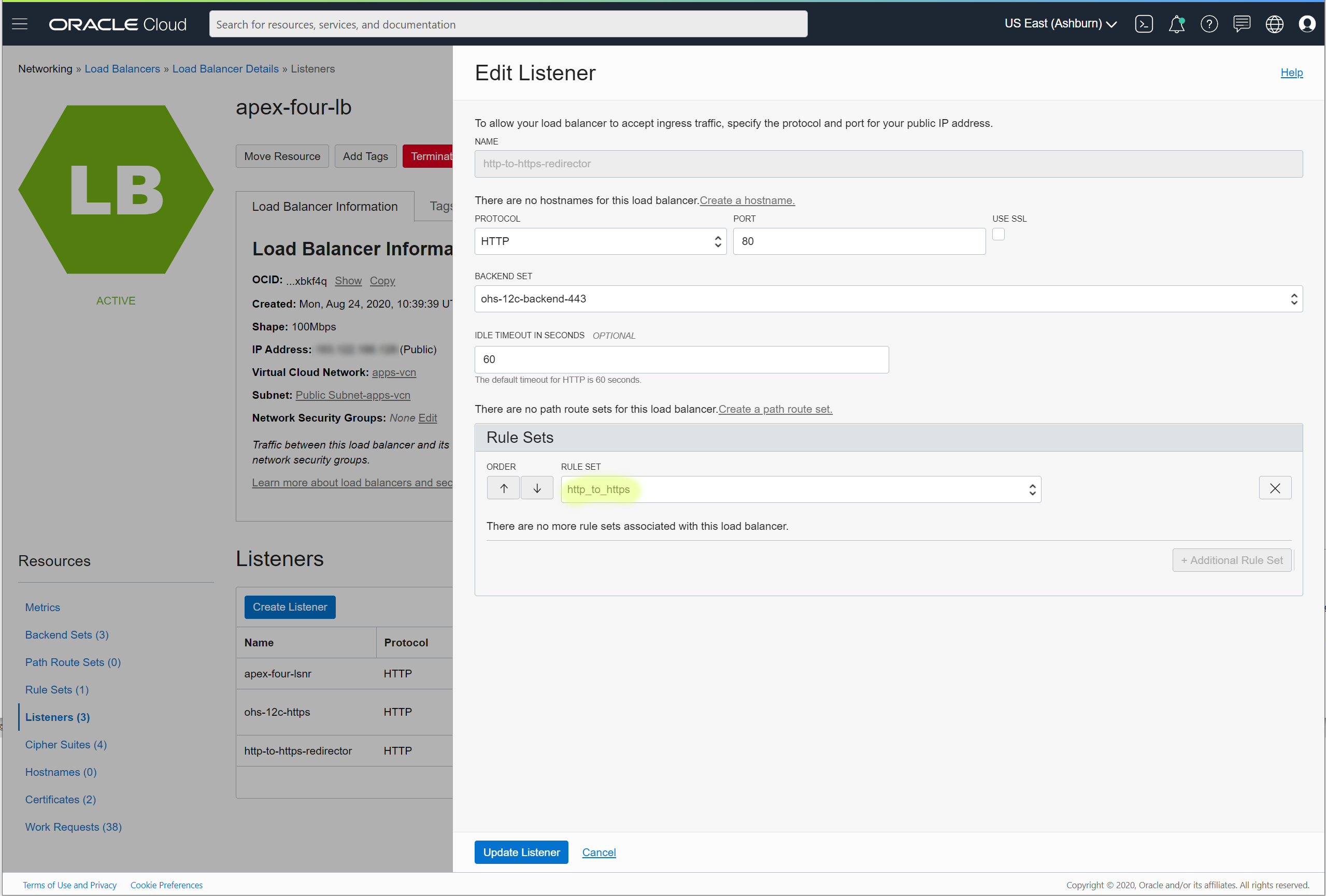
Now the load balancer accepts both HTTP and HTTPS requests with no changes or rewrites on the back-end servers.

