OCI: Secure Load Balancer
It started as a routine wildcard certificate renewal and updating on the Oracle Cloud Infrastructure. It usually takes about 20 minutes, but not today when the certbot offered me a private key update.

It started as a routine wildcard certificate renewal and updating on the Oracle Cloud Infrastructure. It usually takes about 20 minutes, but not today when the certbot offered me a private key update.
I spent most of those twenty minutes remembering how to update wildcard certificates and why the Load balancer states no certificates are configured. Today it started with a private key update offer, presumably, a smart move in the pre-quantum computing era.
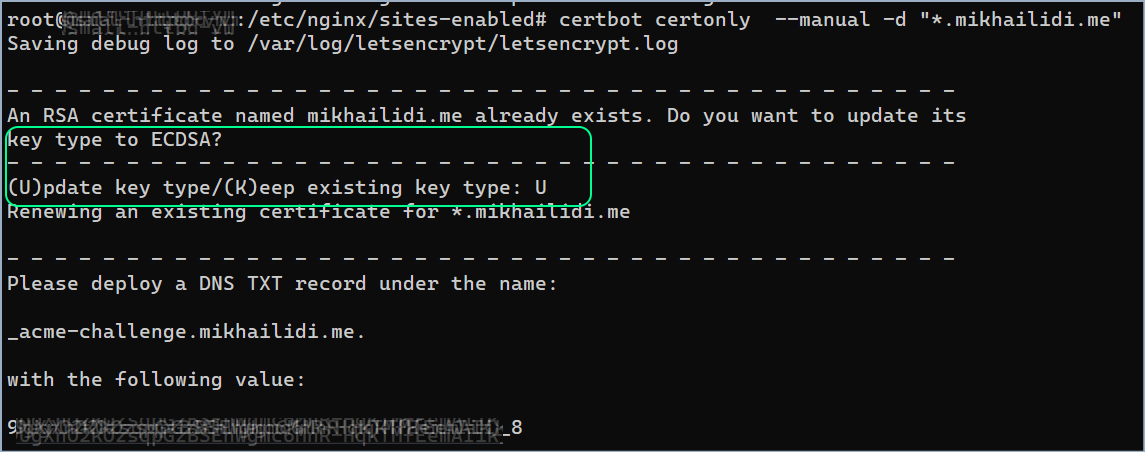
I went through the steps and got my new certificate and key pair. The next step is to create a new load balancer certificate (I don't think regular certificates are allowed on always-free accounts) and instruct the secure listener to use it.
The result was disappointing, and the site threw the error below without reason.
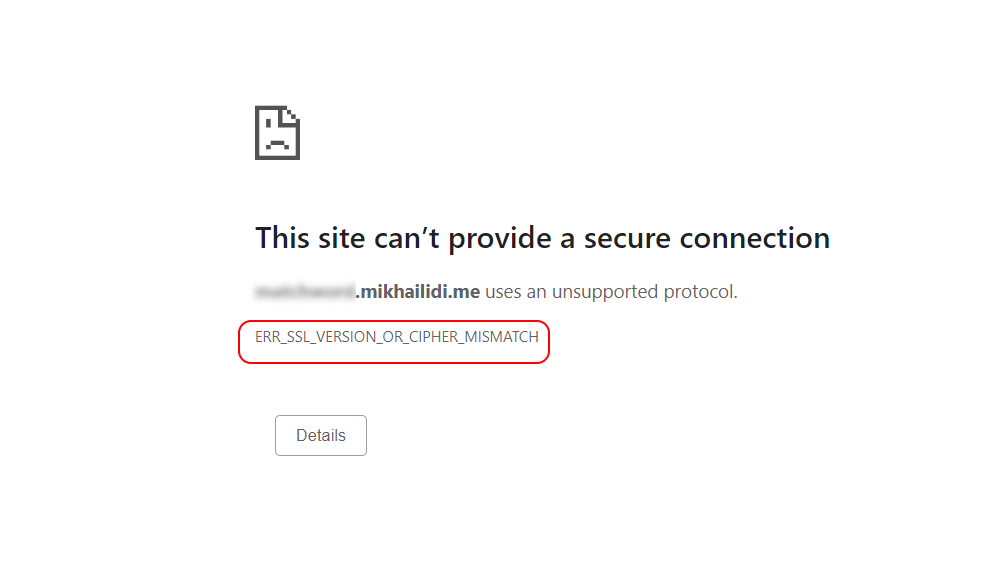
The OpenSSL has no problem with the certificate and private key but threw the "handshake failure" on the load balancer port. The answer was in the listener configuration.
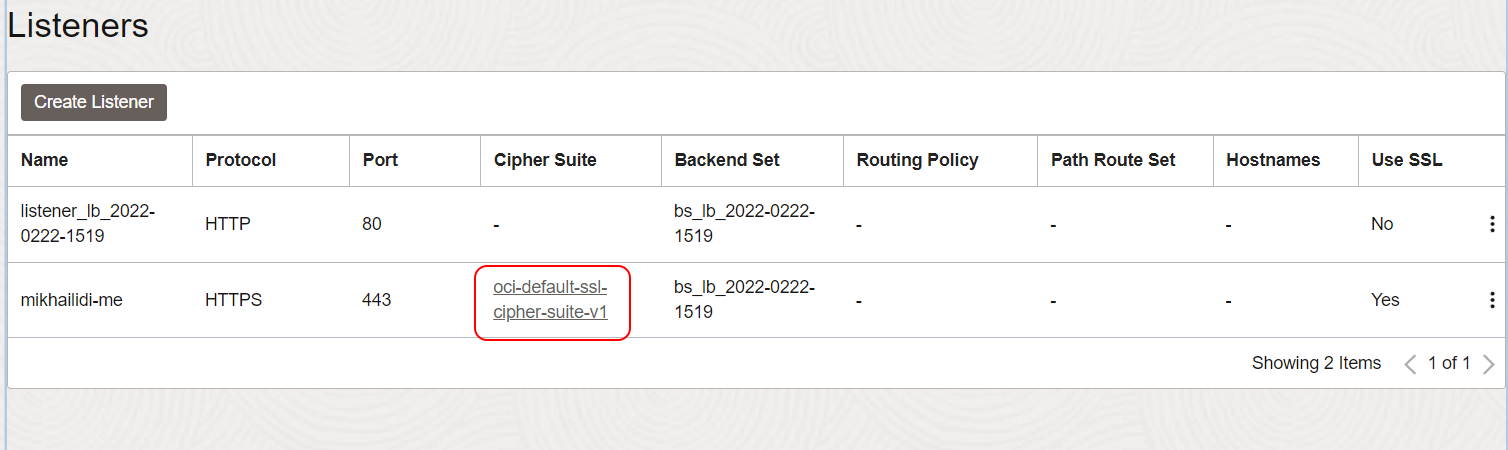
Open listener for edit (three dots on the right), and expand the Advanced Options section. Select the predefined oci-modern-ssl-cipher-suite-v1 or create a custom set of ciphers that meet your security policies.
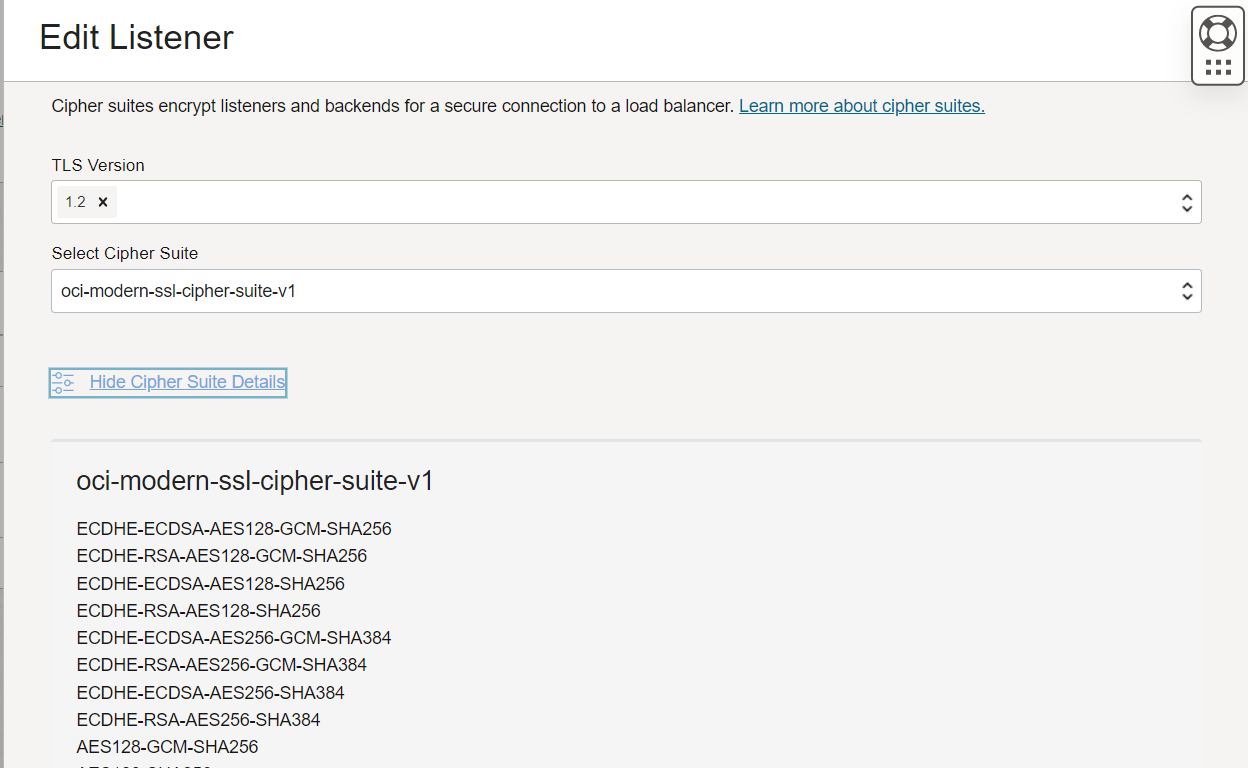
Save the changes and give it a few seconds to propagate the changes. No,w the site is available, and the browser has no issues with the protocols and ciphers.
To summarize: if you make significant certificate changes, ensure that your infrastructure is ready.

